🧵 View Thread
🧵 Thread (10 tweets)
"invests significant resources to obtain [...] less likely to use that identity deceptively"https://t.co/hL1rYmCUXz https://t.co/rQ5l5Qpn6T


"Sybils tend to have a flood of requests [...] then are rejected from legitimate users"https://t.co/y349ymEyhV https://t.co/LUjpEtPRAz


Ants deal with the ant-mimic / interloper problem all the time.https://t.co/jPlEk3QuVs https://t.co/kY9c5sNa1u


Nothing on ants in this, but it does a good job breaking down the problem of sybil attacks:https://t.co/K0r43Gzwx2 https://t.co/KciSk54zzr
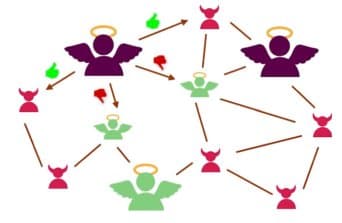
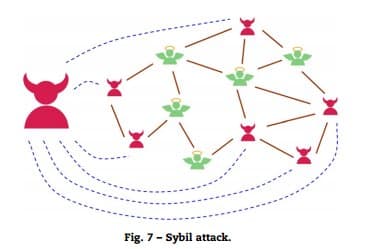

Swarm Intelligence based filtering. https://t.co/H4zqygSka3

Why I feel Sybil attacks are very powerful forces when they run up against filter-bubbles within our networks.https://t.co/xNXd2bXAqS https://t.co/nWDtvSxRgI


Reverse(Aposematic coloration + Batesian mimicry)Decorating like a flower to eat bees.Wolf in sheep's clothing.https://t.co/GNecLbUGyj

"Bee Orchid" https://t.co/hYyIcfnhwR crossed with "Alice and Bob" https://t.co/oTrMNNSnlihttps://t.co/DG3XbYAbu2Eve is actually Sybil? https://t.co/aJcauUOgNu

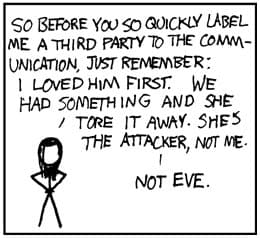

Hmm, xkcd #742 gets close:"it came from inside the Slack!"https://t.co/kQ8WHTlQD2 https://t.co/fsM0Z5307V
