🧵 View Thread
🧵 Thread (10 tweets)
Someone figured out you can spoof sending USDC coin for $0 (and cost of some some txn fees). It makes it look like you sent money to an address.If your software presents it as your own (@Trezor, fix this) and you go back to copy the address absentmindedly...

You can see the signature of this here. They're also targeting USDT. https://t.co/n1JpCSCsc6

It appears that by sending $0, the transaction still gets picked up and reported as coming from your address even tho progenitor of txn doesn't actually have your private keys.You only lose money if you fall for spoof & copy the transaction absent mindedly. It's very creative. https://t.co/QgsvGTyjy2
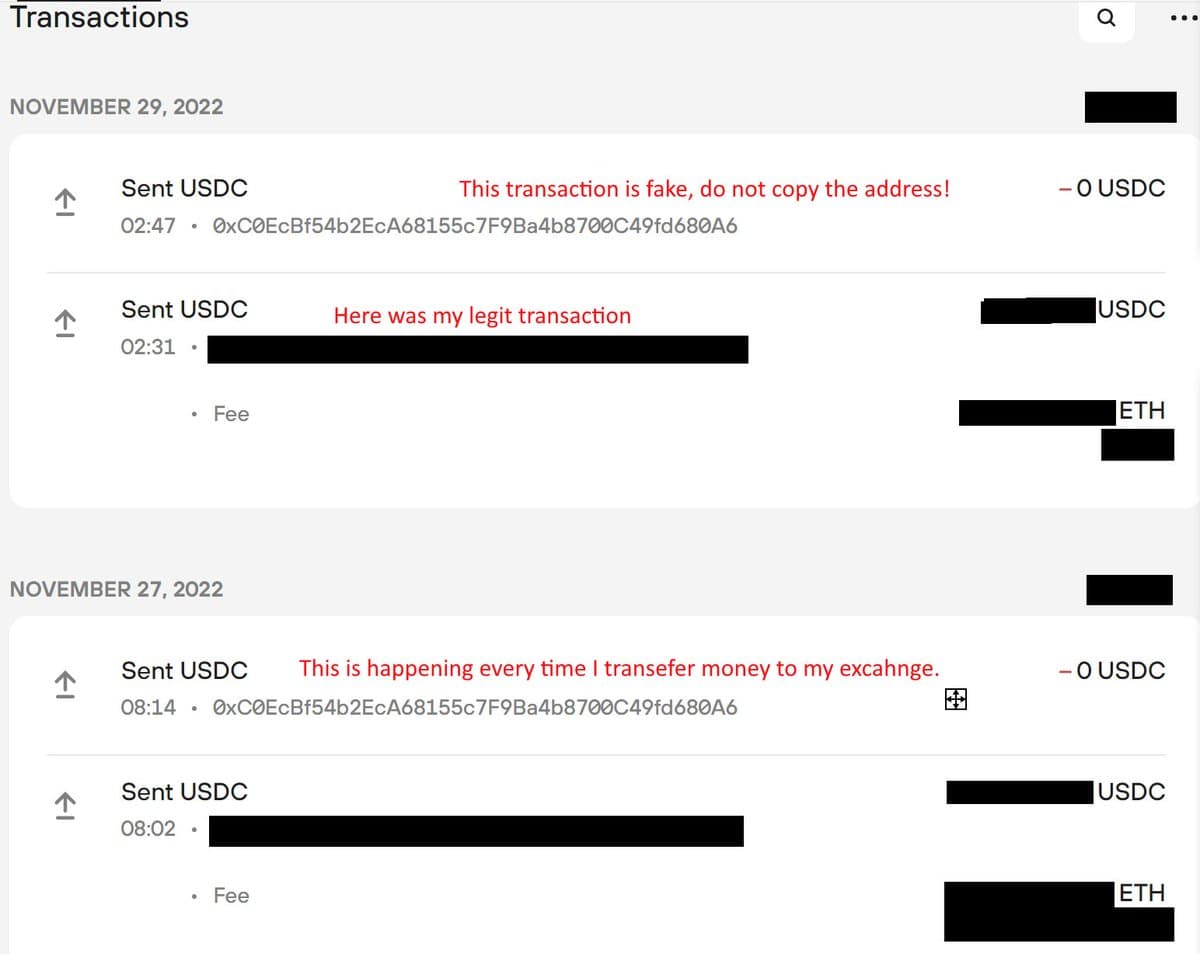

It's a game off odds. If they send enough $0 txns, they'll inevitably find one or two people who are doing that copy/paste behavior. Only takes one moment to not in a sound state of mind (rushed? stressed? ingrained habit?), and then you get pwned.

Weaponizing spam transactions is at least creative. I'll give them that.https://t.co/qqOXghgyyH

Presumably this scam/trap is automated somehow.If someone has some time on their hands, maybe the scammer could be tracked down? Or at least mapping the txns to see how many people have got swindled so far. https://t.co/4z8AybGshg

Looks like this problem also impacts @Ledgerhttps://t.co/wVdt995SO3

Also seems to be targeting multiple networks that support USDT/USDC, not just Ethereum.Presumably any contract that allows a foreign address to "transfer" $0 would allow this to occur.https://t.co/GqC6CtQsz6

I just saw that @trezor fixed this by blurring the transaction out and putting a notice. Seems like a good way to approach this.https://t.co/UX1COXebow